AI + OCT How can artificial intelligence help ophthalmologists diagnose faster and more accurately?
The combination of artificial intelligence (AI) and optical coherence tomography (OCT) is revolutionizing the diagnostic model of ophthalmic diseases. The core of this integration lies in combining the powerful data analysis capabilities of AI with the high-resolution biological tissue structure imaging of OCT, thereby providing doctors with insights that exceed the limits of human vision. Specifically, AI has provided revolutionary assistance in the following aspects
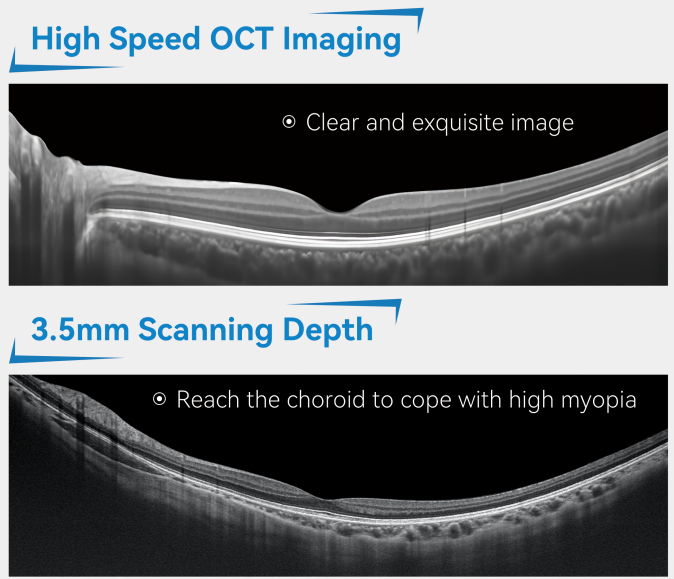
I. Core Support: Faster, More Accurate, and Smarter
1.Ultra-high-speed quantitative analysis and screening
What to do: AI algorithms can automatically complete the analysis of the entire OCT three-dimensional volume scan within seconds, accurately segment each layer of the retina structure (such as the nerve fiber layer, photoreceptor cell layer, etc.), and measure its thickness and volume.
Traditional pain points: Manual measurement by doctors is time-consuming and labor-intensive, and it is difficult to quantify the entire retina so precisely.
The changes brought about: It provides objective and repeatable quantitative data for glaucoma (focusing on the optic disc and nerve fiber layer) and macular diseases (focusing on the thickness changes of each layer), greatly shortening the initial assessment time.
2. Anomaly detection and lesion identification
What to do: The AI model, trained on a vast amount of labeled data, can automatically identify and label various lesions in OCT images like an experienced expert, such as
Diabetic macular edema: Detection of fluid accumulation within the retina (cystoid edema).
Age-related macular degeneration: Identification of vitreous warts, subretinal fluid, choroidal neovascularization, etc.
Retinal vein occlusion: Macular edema and hemorrhage are found.
Macular holes, epiretinal membranes, etc.
The changes brought about: AI can act as the "first reader", quickly marking suspicious lesion areas, preventing the missed diagnosis of tiny lesions due to visual fatigue or lack of experience, and is particularly suitable for large-scale community screening.
3. Disease classification and severity grading
What to do: AI can not only detect lesions but also automatically classify and stage diseases. For instance, to determine whether AMD is dry or wet, to grade the risk of visual field defects in glaucoma, or to assess the severity of diabetic retinopathy.
The changes brought about: It provides doctors with standardized diagnostic references to assist in making treatment decisions and priorities (for example, which patients with wet AMD need urgent anti-VEGF treatment).
4. Predict disease progression and treatment response
What to do: This is the most cutting-edge application of AI. By analyzing the longitudinal OCT sequence images, the AI model can learn the patterns of disease development and predict the risk of future disease deterioration. At the same time, it can also predict the possible response of patients to specific treatments, such as anti-VEGF injections.
The changes brought about: achieving a leap from "diagnosing the present" to "predicting the future", making personalized medicine and preventive intervention possible.
Ii. Specific Manifestations in the Clinical Workflow
In screening scenarios: AI-OCT systems can be deployed in communities or physical examination centers. OCT scans are operated by technicians, and AI generates reports in real time, quickly screening out high-risk patients for referral to specialists, greatly improving the efficiency and coverage of screening.
1.In the outpatient setting:
Before the examination: The patient has completed the OCT scan.
2. During the examination: AI real-time analysis generates a preliminary report with color annotations, quantitative data, and suspicious findings before the doctor's consultation.
3. Doctor's Diagnosis: Doctors do not need to analyze from scratch from a vast amount of raw data. Instead, they directly review the AI's findings and, based on their own clinical experience, confirm, correct and make a final diagnosis. This is equivalent to having an "indefatigable assistant" complete all the basic measurements and initial screening work.
4. Follow-up Comparison: AI can automatically and precisely match and compare this scan with the patient's historical scans, highlighting the areas that have changed (improved or deteriorated), making the follow-up assessment clear at a glance.
Iii. Core Values for Ophthalmologists
1. Liberate productivity: Free doctors from heavy repetitive labor (measurement, comparison), allowing them to focus on decision-making, doctor-patient communication, and treatment plan formulation that require high-level clinical thinking.
2. Enhance diagnostic capabilities: As the "second pair of eyes", it provides objective and quantitative decision support, reduces diagnostic differences among individuals, and improves the consistency and accuracy of overall diagnosis.
3. Dealing with the data deluge: Modern OCT scans generate an enormous amount of data, and AI is an indispensable tool for processing and analyzing these big data.
4. Empowering grassroots and non-experts: Assist grassroots hospitals or general practitioners in initially identifying complex eye diseases, promote hierarchical medical treatment, and enable more patients to receive correct referral advice in a timely manner.
Also welcome to contact us, we are ZD Medical Inc.
Tel : +86-187 9586 9515
Email : sales@zd-med.com
Whatsapp/Mobile : +86-187 9586 9515